Facebook and LinkedIn users will want to remain vigilant as a randomware that is described as low-tech but cunning is spreading rapidly through the websites over the past week.
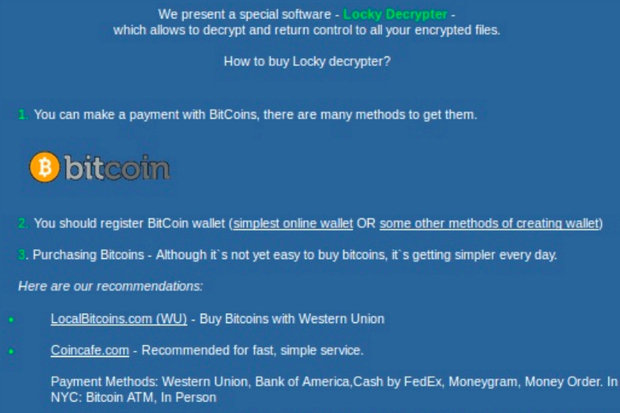
Dubbed ImageGate, the exploit was first detected by researchers working for an Israeli security firm called Check Point. In this exploit, the attackeds would embed malicious code into an image file and upload it onto the social media website. The attackers would then exploit a misconfiguration on the social media infrastructure which forces the user to download the image file. Should the image file be opened, said malicious code would begin installing a ransomware called “Locky” onto their computers. What happens after that is standard operating procedure for a ransomware. Locky would encrypt the user’s files and the user would be force to pay a certain amount of bitcoins in order to decrypt the files.
Curiously enough, Facebook has since responded to these supposed randomware attacks, suggesting that the case is merely a matter of “bad Chrome extensions.” In a statement issued to Engadget, Facebook claims that reports about these attacks were investigated and it was discovered that the attacks were due to several bad Chrome extensions. Facebook went on to mention that they’ve been blocking said extensions for nearly a week and have since reported the extensions to the appropriate parties. LinkedIn has yet to comment on the matter.
In the meantime, Facebook and LinkedIn users should refrain from opening any file that has been automatically downloaded, particularly image files with the SVG, JS, or HTA extensions.
Source: Ars Technica, Engadget, Check Point